
FOR ANY SIZE OF BUSINESS
SIMPLE TO IMPLEMENT
No matter the size of your company

Devices always up to date with the latest security fixes and stability improvements. This helps keep the network safe from threats and performing at peak performance.
Meraki devices such as wireless access points, switches, and firewalls automatically receive firmware updates directly from the Cisco Meraki cloud. This includes security improvements, bug fixes and new features.
While updates are automatic by default, you can also choose to schedule when firmware updates will be applied to your devices. This allows you to choose a time that is most convenient for your operation. Easily revert to a previous firmware version if an update causes issues.
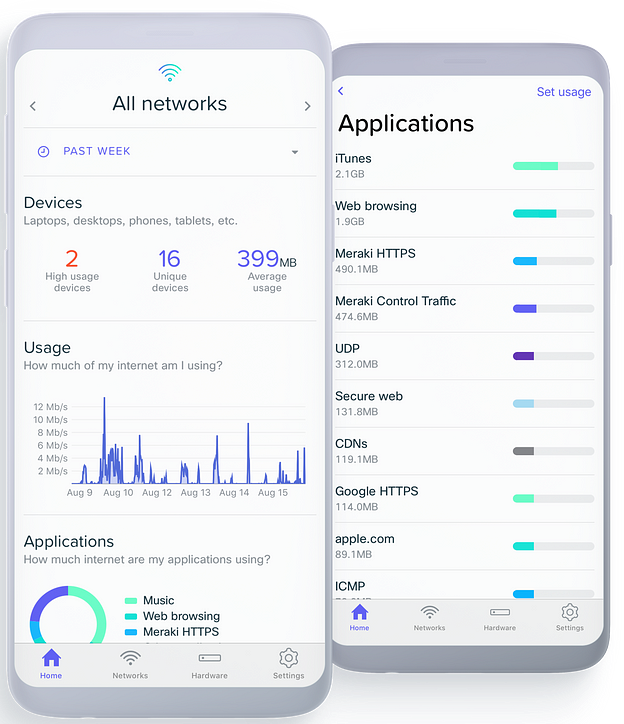

Meraki offers advanced analytics and insight capabilities that allow network administrators to gain a deeper understanding of traffic, network performance and device behavior.
The Meraki platform provides detailed information about network traffic, including upload and download data, types of applications in use, protocols, traffic source and destination, and much more. This allows you to understand how network resources are being utilized and identify potential bottlenecks.
Meraki monitoring dashboards provide a real-time view of network traffic, device status and connectivity. This allows you to quickly detect problems and take action to ensure the smooth running of the network.
Provides details about devices connected to the network, including information about device type, operating system, application usage, connection history, and more. This helps identify malicious devices or anomalous behavior.
The platform keeps a log of relevant events such as firmware updates, configuration changes and security events. This helps to keep track of network activity and changes, identifying potential threats and suspicious network activity.
